Heartbleed Bug – the what, the hack, the fix
What is it?
You may have heard about the Heartbleed bug; the recently discovered OpenSSL vulnerability that could potentially allow attackers’ access to supposedly secure servers, such servers that will often house emails, passwords, credit card details and more. If that doesn’t sound scary enough, it gets worse, experts believe this bug has been exploitable for the last two years!
Being a little more specific, an attacker could pass in an incorrect value to an OpenSSL extension and they could proceed to read up to 64KB of the target hosts RAM. The attacker can just loop through this process to expose more and more memory to gather your personal data (or whatever else they have stored) and essentially act as a ‘man in the middle’, something SSL was designed to detect.
Just to be clear, Heartbleed isn’t a core issue with SSL/TLS encryption, it’s an issue with the OpenSSL implementation, more specifically the version released March 14, 2012 version 1.0.1, the bugs’ official reference is CVE-2014-0160.
The reason this bug is so profound is the fact that it has potentially allowed secure data to be leaked out for the last 2 years and all undetectable and untraceable. The flaw was actually discovered by an independent research team of security engineers at Codenomicon along with a member of Google Security team.
Getting Hands on!
We decided to try out our hacking skills and see if we could download the memory of a vulnerable server by exploiting the Heart bleed bug, it turns out there’s a no-hacking-skills-required policy! After a couple of searches online we found a Python script that would do the job for us, after about 3 minutes of effort (if that) we had our script running against well-known sites, sadly a lot of them were still vulnerable and happily handing over their data.
Here is a memory dump from one of the sites we found (I’ve blocked out their identity and blanked out bits of info).
As you can see there is Cookie information in here, all we’d need to do is copy that Cookie into our own browser and we could log in as that user – Essentially Session Hijacking.
Something that really stuck out to me was the speed in which you can pull this data, you can run the script to keep hitting the server in quick successions – that is really quite astonishing, and each one will provide more data.
The thing to note here is that you don’t need to be a hacker to run these scripts, so anyone could potentially be stealing your data and all untraceable in your log files.
From a marketing perspective this is a good reminder of the importance of a good name, how we see it, this has spread so far for two reasons; the size of the vulnerability, and its branding. Just look at google images…
I’ve not seen a bug this well publicised this much since the millennium bug. The bugs’ official name being CVE-2014-0160 is nowhere near as sexy as Heartbleed! This of course is bitter-sweet, on the one hand it’s spreading awareness and hopefully pushing businesses and the like, to secure their servers but on the other hand now every man and his dog knows about it too and as we have already shown you it’s incredibly easy to do.
How to patch the leaks?
Site owners
To fix this bug so you are not at risk, you need to update to the latest version of OpenSSL version 1.0.1g, released on April 7, 2014. If you are running the old version you need to update as soon as possible. The information on this bug is now wide spread and there will be attackers out there trying to take advantage of those who are slow to respond and update.
If for whatever reason you are unable to upgrade to the new version immediately, you can recompile OpenSSL with -DOPENSSL_NO_HEARTBEAT. We have put together a testing app below to test your site if you’re not sure if you are vulnerable or not.
Users
The chances are you will be unaffected, that’s what we’d like to believe of course and only wishful thinking. You should begin running through your accounts and changing passwords and potentially think about not using some online services if you think a site or service may still be affected by this bug and don’t just think online shopping baskets, the encryption library is used on apps too such as emails and online accounts such as YouTube and more, to readdress what I have said above, this vulnerability is now common knowledge and undetectable (if you don’t know what you are looking for), meaning if a site is unprotected, you are just leaking your private data to the world.
Testing your site
We decided to put together a testing interface so you can test your own sites for the vulnerability, this is using the Python script mentioned above and it will show you the memory dump if the server is vulnerable and hopefully show just how important this is to fix! If you use this on your own sites and it helps you then great but if you decide to run this against sites you don’t own, you do so at your own risk and We Take No Responsibility!
Apologies the tool is no longer available as it stopped working 🙁
Share this article
Like what you’ve read, then why not tell others about it... they might enjoy it too
We'd love to hear from you!
If you think Bronco has the skills to take your business forward then what are you waiting for?
Get in Touch Today!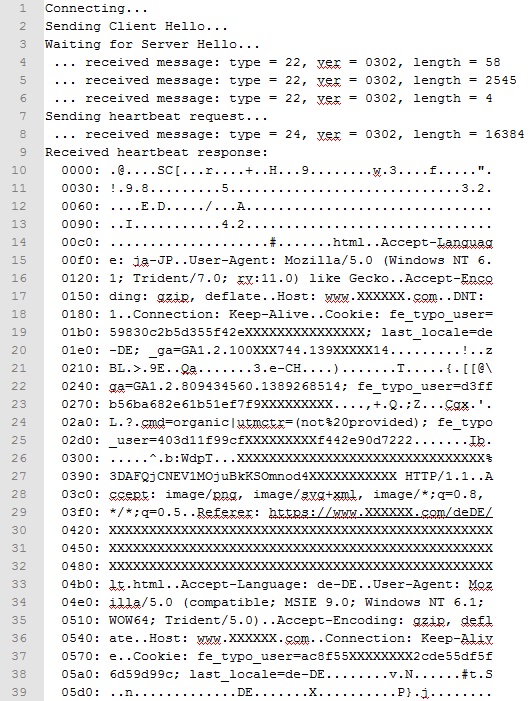
Discussion